SSH to Private EC2 Without Bastion Hosts
How I use EC2 Instance Connect Endpoint to access private instances without NAT gateways or bastion hosts.
I used to deploy bastion hosts for SSH access to private instances. Then I had to patch them, rotate keys, and manage security groups. NAT gateways for outbound-only traffic felt wasteful at $32/month just for SSH access.
EC2 Instance Connect Endpoint is cleaner. No bastion, no NAT, no public IPs. SSH into private instances directly through AWS PrivateLink.
How It Works
You create an endpoint in your VPC. The endpoint lives in your private subnet and acts as a tunnel for SSH connections. Traffic never leaves AWS's network.
From your laptop, you connect to the endpoint, which forwards the connection to your private instance. No internet gateway involved.
Setting It Up
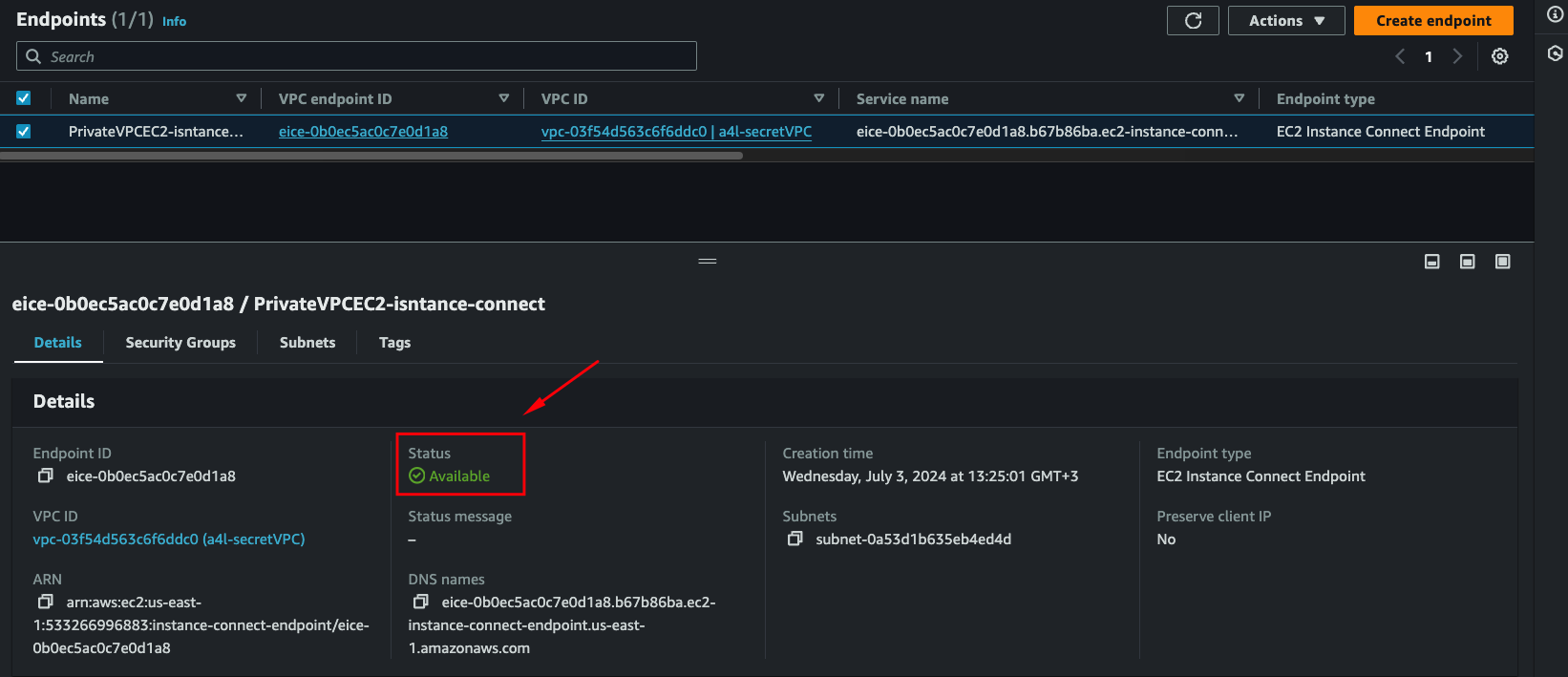
1. Create the endpoint:
VPC Console → Endpoints → Create Endpoint
- Service: EC2 Instance Connect Endpoint
- VPC: Your target VPC
- Subnet: Where your private instances live
- Security group: Allow SSH from your source
Wait 3-10 minutes for provisioning.
2. Configure security groups:
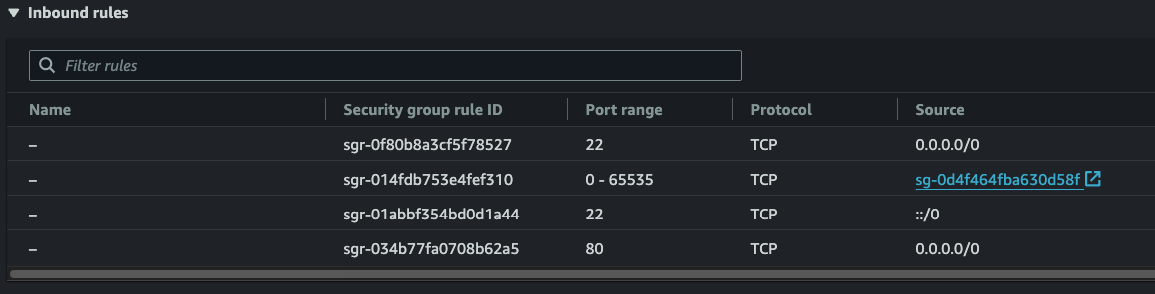
Instance security group needs:
- Inbound SSH (22) from the endpoint security group
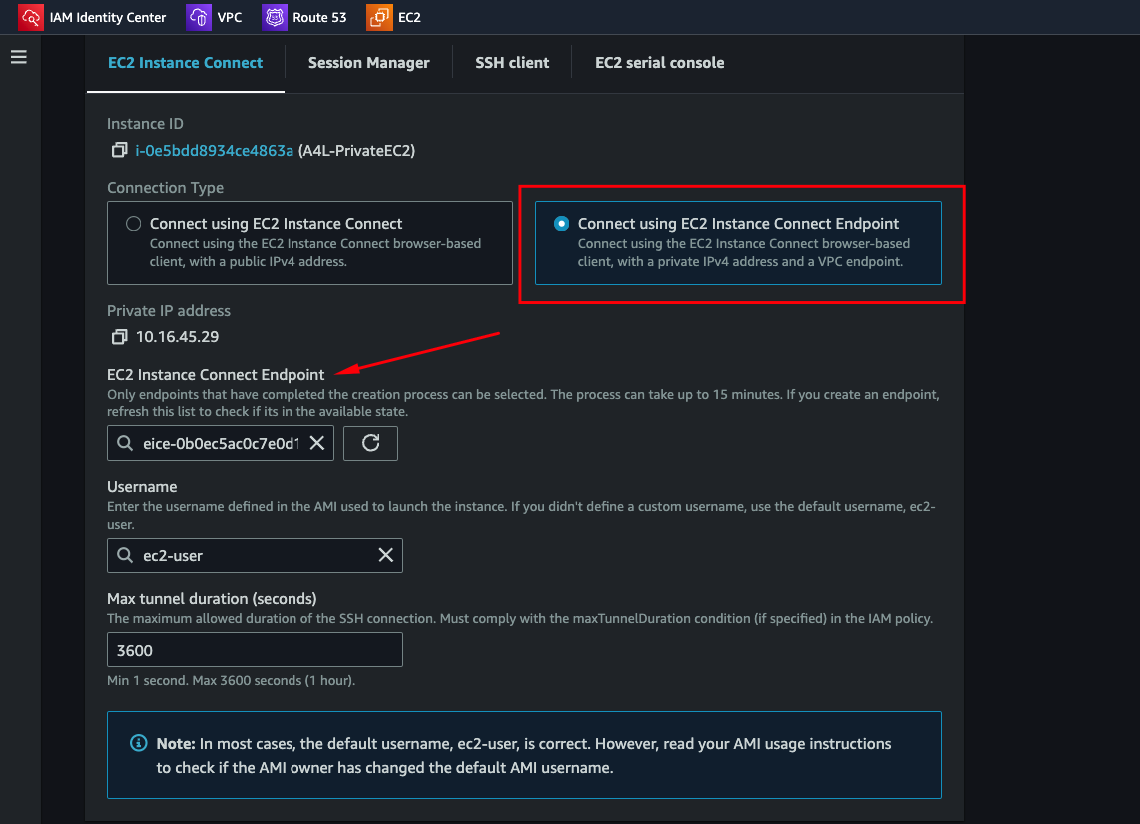
3. Connect:
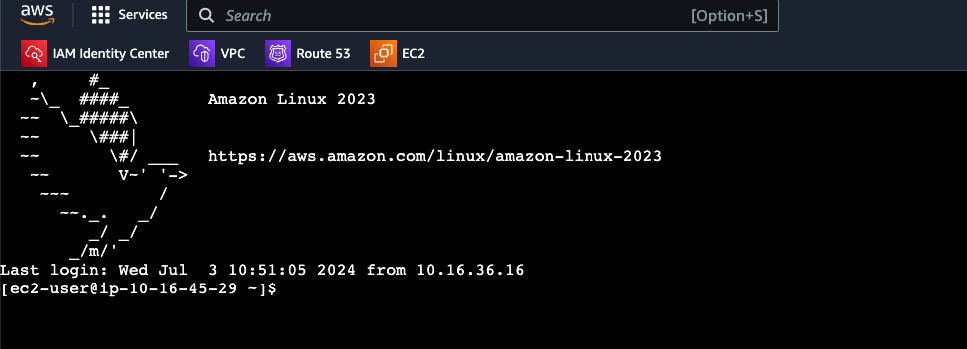
From the EC2 console, select your instance and click Connect. Choose EC2 Instance Connect Endpoint.
Or use the CLI:
aws ec2-instance-connect ssh --instance-id i-0123456789abcdef0
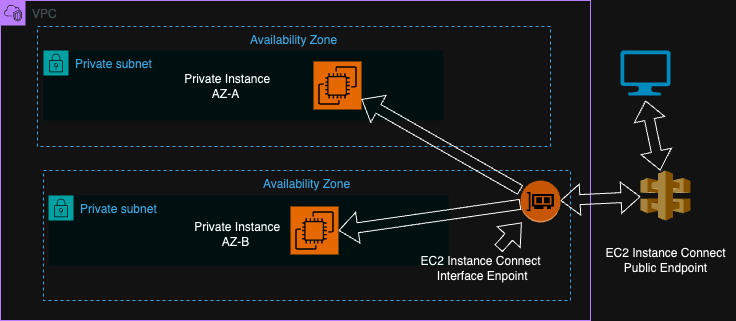
Why I Prefer This
No bastion to maintain. Bastion hosts need patching, key rotation, and monitoring. The endpoint is managed by AWS.
No NAT costs for SSH. NAT gateways charge per hour and per GB. For occasional SSH access, that's expensive.
Cleaner security model. Traffic stays within AWS. No public IPs on anything.
IAM-controlled access. You can restrict who can use the endpoint with IAM policies, not just security groups.
Limitations
- Only works with EC2 Instance Connect (not traditional SSH keys)
- Endpoint costs ~$7/month
- One endpoint per VPC (can reach any instance in the VPC)
For environments where I previously ran bastion hosts, the endpoint pays for itself quickly.
Key Takeaways
- EC2 Instance Connect Endpoint provides SSH to private instances without bastion hosts
- Traffic stays within AWS via PrivateLink - no internet exposure
- Costs ~$7/month vs $32+ for NAT or bastion maintenance overhead
- Access controlled by both security groups and IAM policies
- Works with AWS CLI:
aws ec2-instance-connect ssh --instance-id i-xxx
Written by Bar Tsveker
Senior CloudOps Engineer specializing in AWS, Terraform, and infrastructure automation.
Thanks for reading! Have questions or feedback?